Penetration Testing

Cybercriminals can penetrate 93% of company networks
What happens if an attacker breaches your network through a successful phishing attempt or otherwise? How exposed are your data and systems to further exploitation? How vulnerable are your key internet-facing applications and infrastructure to attack from cyber criminals?
An expert-led penetration test from Slipstream Cyber will simulate the techniques real attackers use to answer these questions and provide actionable advice on the risk and remediation options.
Our reports are written in plain English to enable non-technical audiences to understand the results and risks, whilst containing all the technical details required for remediation.
Comprehensive Penetration Testing services
External Network Testing
Internal Network Testing
Application Security Testing
Adversary Simulation (Red Teaming)
Office 365 Security Assessments
Bespoke Testing

Strengthen your defences with Slipstream Cyber
Cyber threats are constantly evolving—so should your security. Slipstream Cyber’s Penetration Testing Services go beyond vulnerability identification to provide a tailored approach that enhances your organisation’s resilience, ensures compliance, and protects critical assets.
Why choose Slipstream Cyber?


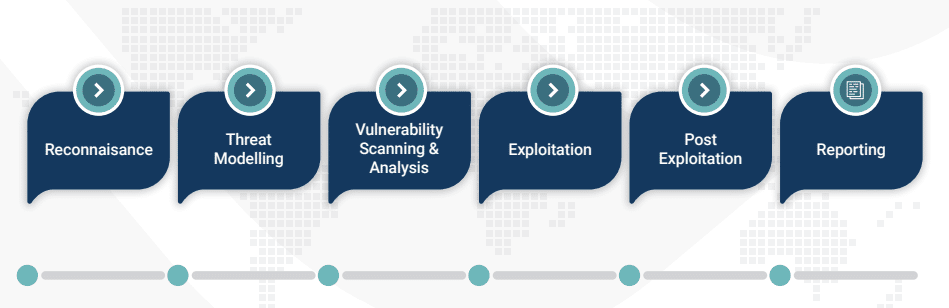
Our Penetration Testing approach
- Customised Assessments: Tailored to your organisation’s specific risks and environment.
- Realistic Attack Simulations: Test your defences against real-world cyber threats, including Red Teaming exercises.
- Actionable Insights: Receive clear, prioritised remediation plans to strengthen security.
- Integrated Strategy: We align with your people, processes, and technology to build a cohesive security framework.
Who benefits from our services?
- Cybersecurity leaders: Align stakeholders, optimise investments, and proactively manage risks.
- Enterprise organisations: Enhance resilience, ensure business continuity, and build customer trust through a strong security posture.
How our process works
- Discovery & planning: We align with your objectives and gather critical information.
- Testing & simulation: Our experts simulate real-world attacks on your systems.
- Analysis & reporting: Receive a detailed report with prioritised remediation steps.
- Remediation support: We guide you in strengthening security and closing vulnerabilities.



